Pfsense - Connect to VPN PIA

This tutorial use : https://www.privateinternetaccess.com as VPN but the operation will be mostly the same with another provider.
I will explain how to connect your PfSense to PIA VPN and chose which device you want to "protect" with.
In this tutorial I'll use the recommanded ciphering, for a balance use of CPU / security.
The plan
Here's the setup without VPN, normal PfSense, allow devices from LAN and DMZ to go on WAN.
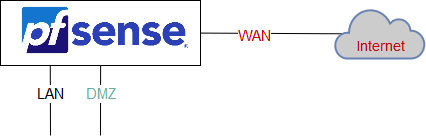
We want : a second PfSense, dedicated to permanent VPN connexion.
The PfSense at the top is the default gateway of all device / server, nammed pfsense.pla01.lbdg.lan. We're gonna use him to route some servers / devices into the VPN.
The PfSense at the bottom will be the VPN, he use the DMZ interface, to have an internet connexion.
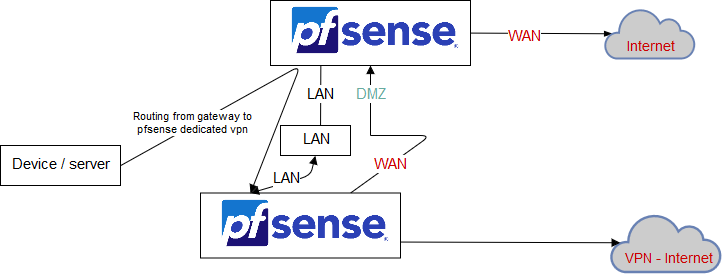
Informations
| Hostname | LAN IP address | Theme | Description |
|---|---|---|---|
| pfsense.pla01.lbdg.lan | 10.0.0.1 | Normal | default gateway of all my devices (on the top of the scheme) |
| pfsense-vpn-tuto.pla01.lbdg.lan | 10.0.0.5 | Red | pfsense dedicated for the VPN (on the bottom of the scheme) |
I use different PfSense theme, it helps to see the difference between the two PfSense
Import certificate authority
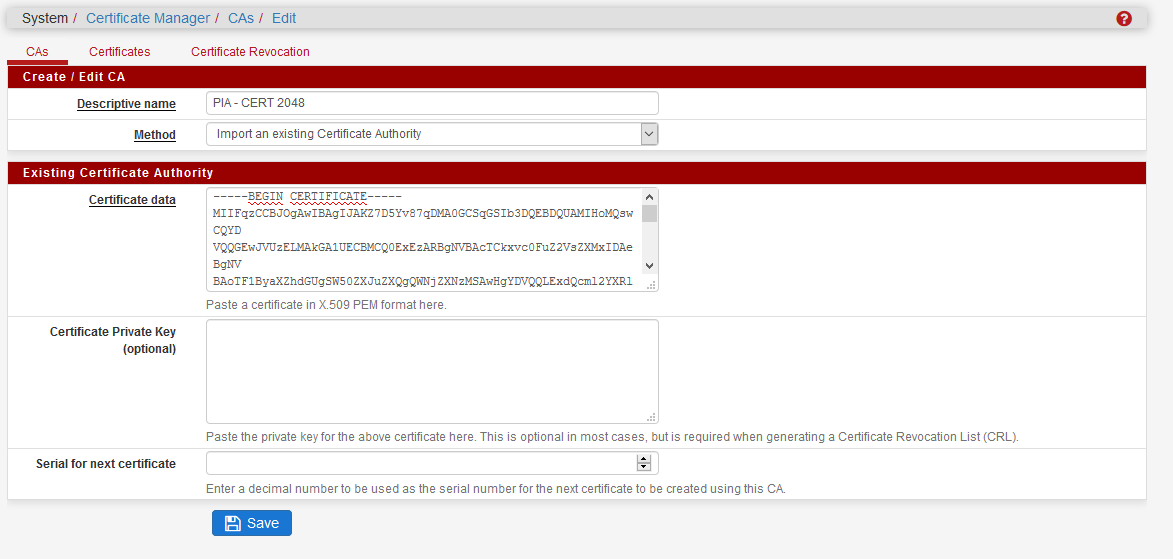
First, you should download and import the PIA CA on your PfSense (so, all the certificate from signed from this CA will be accepted).
Here you can find the CA : https://www.privateinternetaccess.com/openvpn/ca.rsa.2048.crt (right click, save the target as)
Now, you need to open the ca.rsa.2048.crt file with a text editor, and copy the content in the clipboard.
On pfsense-vpn-tuto, go to : System => Cert. manager
In certificate data, paste CA file content
Choose the server you want
PIA give you the choice of lot of server, here's the page to choose : https://www.privateinternetaccess.com/pages/network/
First, I wanted use a server from US, so I tested it out some :
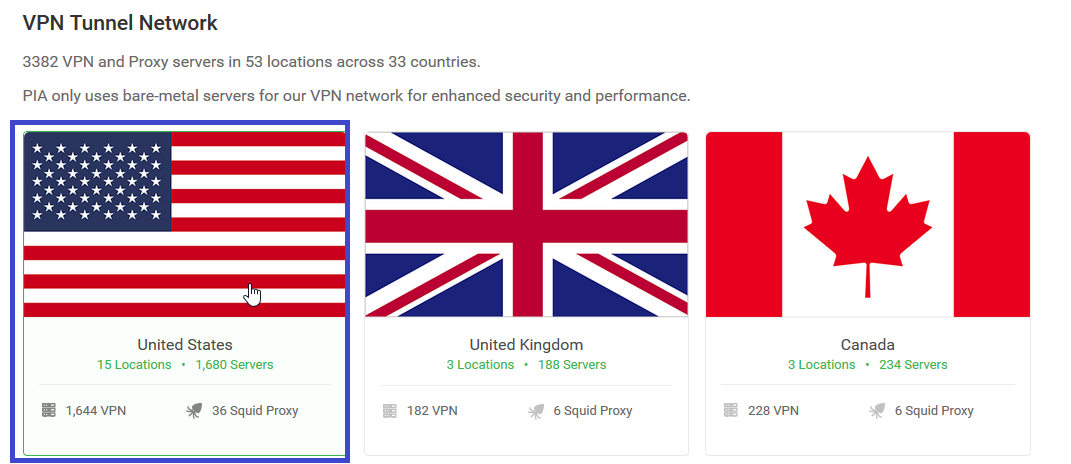
Random server, in California
Run the test
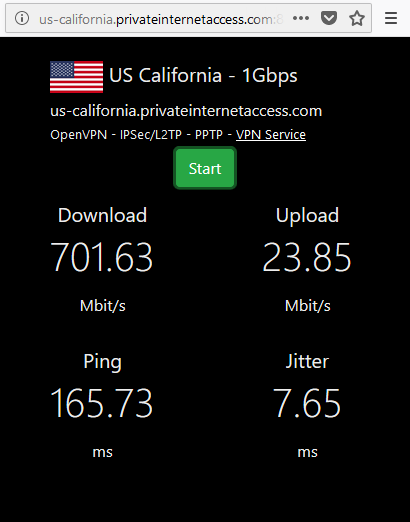
And ... The result is pretty bad (ping = awfull)
I made some others tests, and finally find the good one :
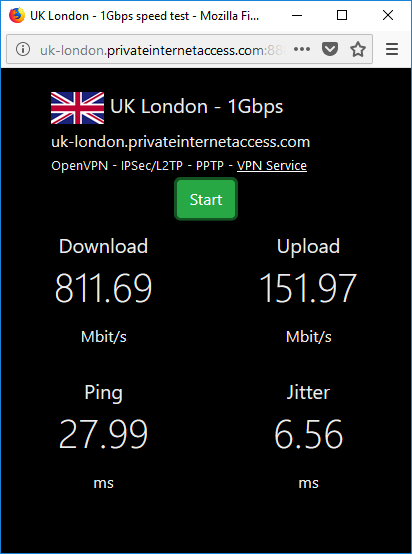
The VPN server is : uk-london.privateinternetaccess.com (remember this)
Connect to VPN
In the VPN configuration, scroll to OpenVPN => Client, add a new client
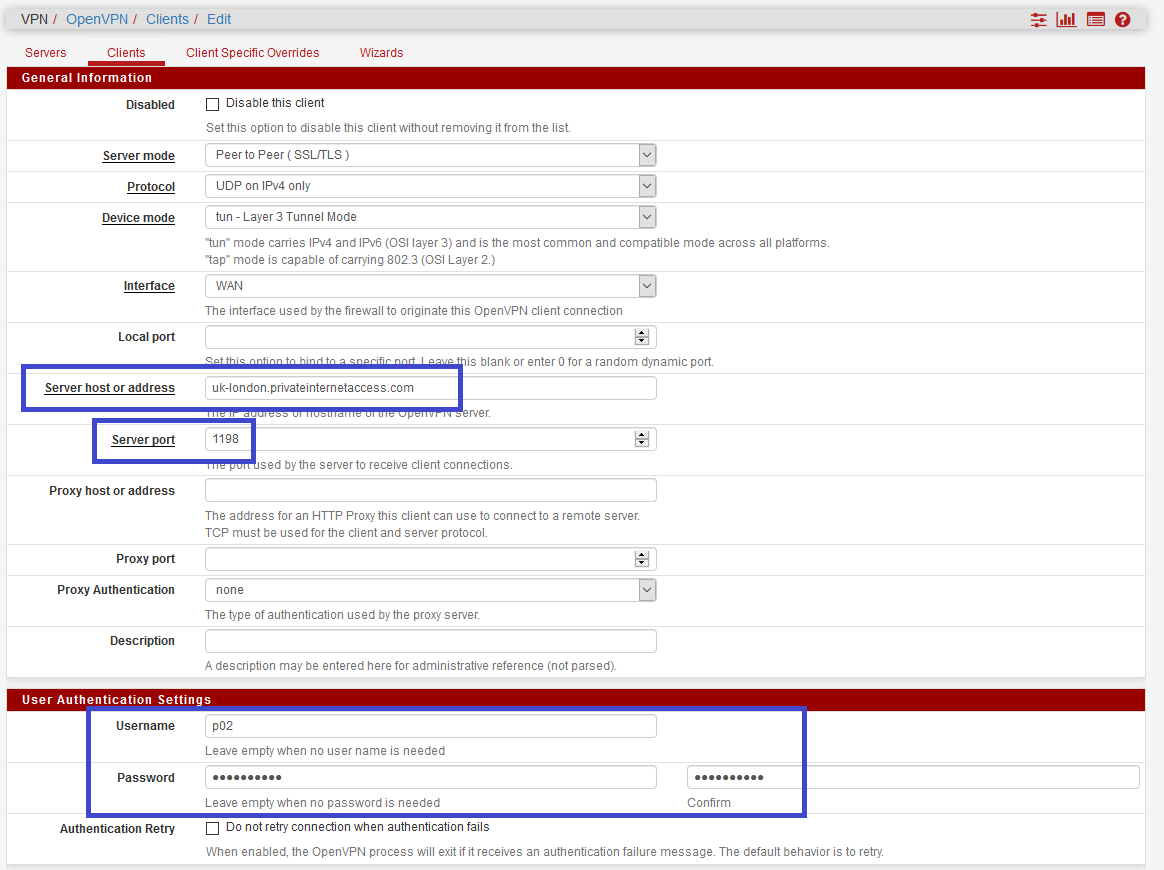
You need to fill :
- the hostname server retrieved from the tests (uk-london.privateinternetaccess.com)
- the port 1198
- your username and password from PIA
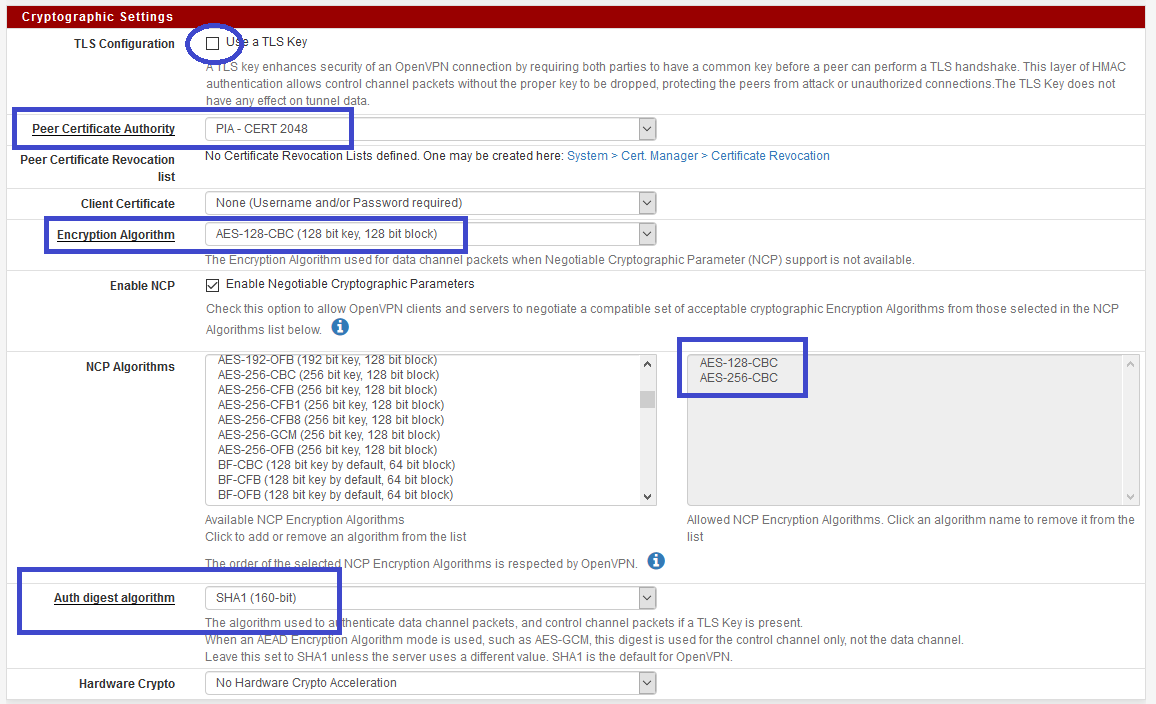
PIA don't use TLS key, so, uncheck it.
They'll use AES-128-CBC (which is pretty good) and NCP with algo : AES-128-CBC & AES-256-CBC. Auth digest should be sha1.
For hardware crypto, it will depend on your hardware, but use BSD cryptodev engine if can
Leave Tunnel Settings by default
In the adanced configuration
Add following parameters to the custom options :
persist-key
persist-tun
remote-cert-tls server
reneg-sec 0
Use fast I/O AND change buffer size, the perfect balance for me, is 1 MB.
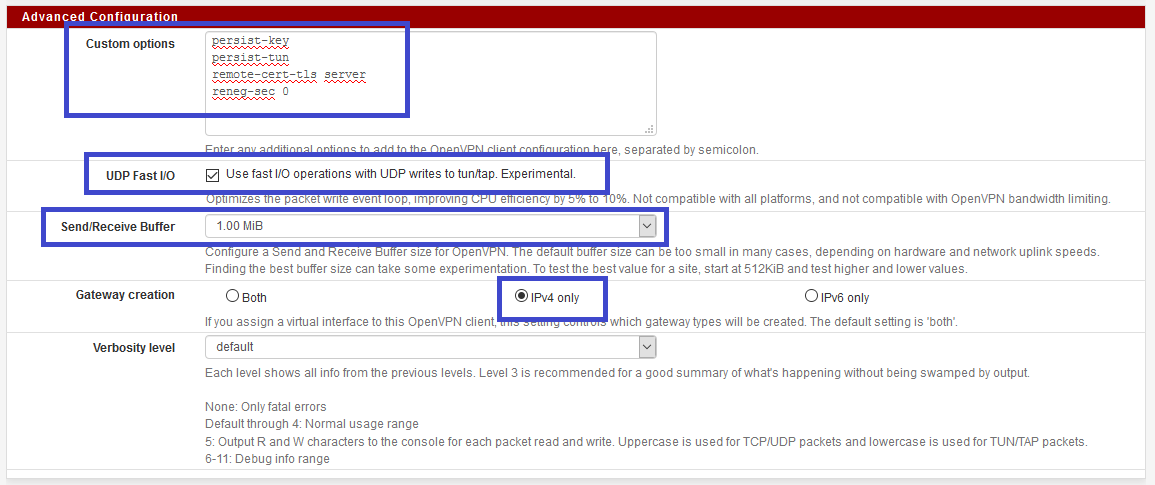
And, hit save button.
Now, we need to check if the VPN is mounted. Click on status, scroll to OpenVPN :
If the status stay down it migh be a configuration problem / port opening through WAN.
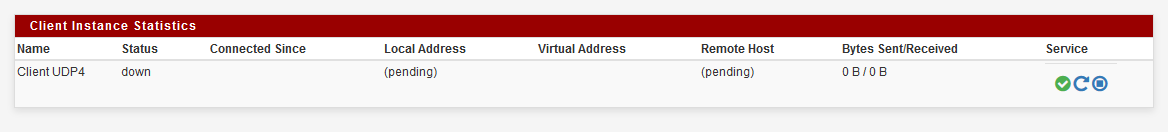
Otherwise 
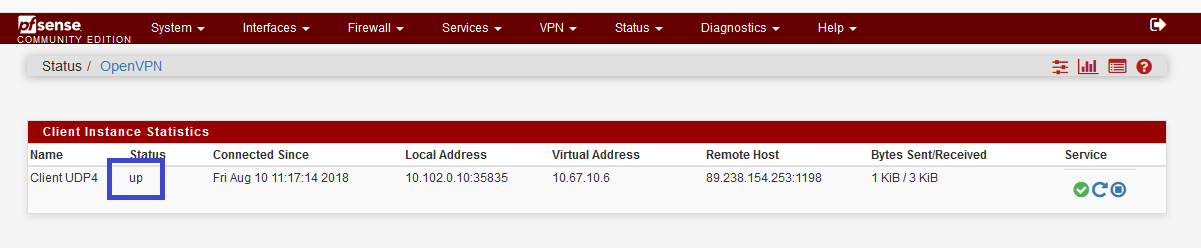
The VPN is now up and running !
Access the VPN
We are now connected to a new "gateway". So we need to configure NAT, to permit device to NAT on this "gateway".
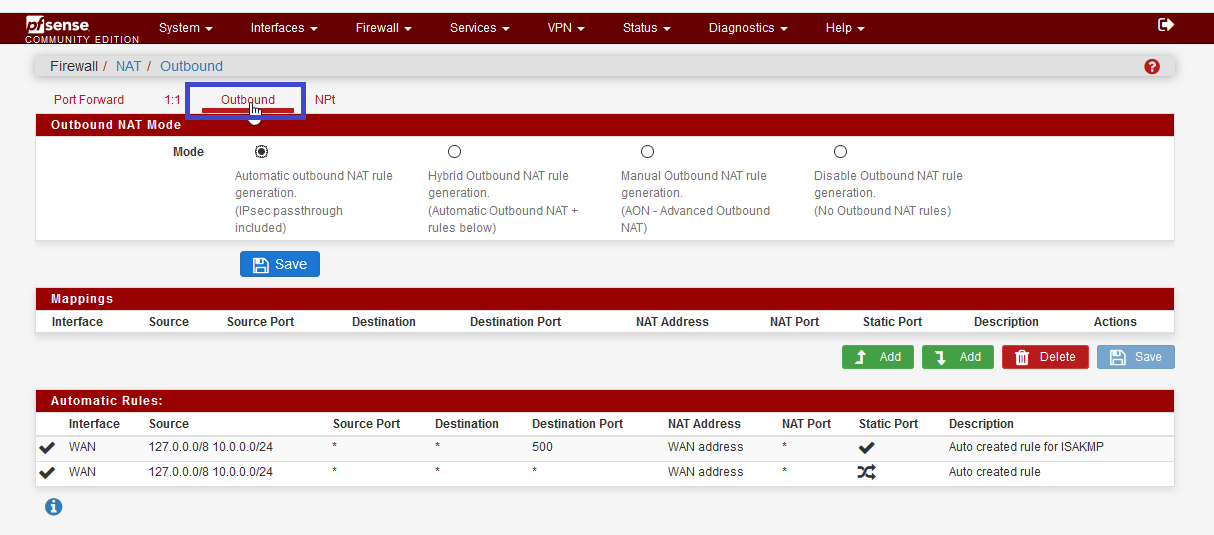
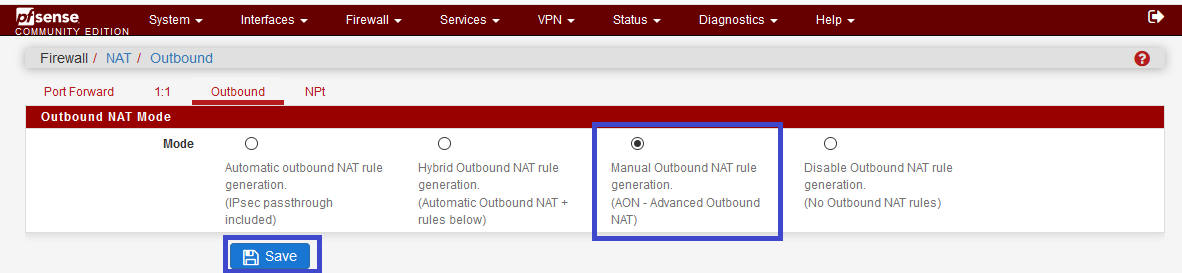
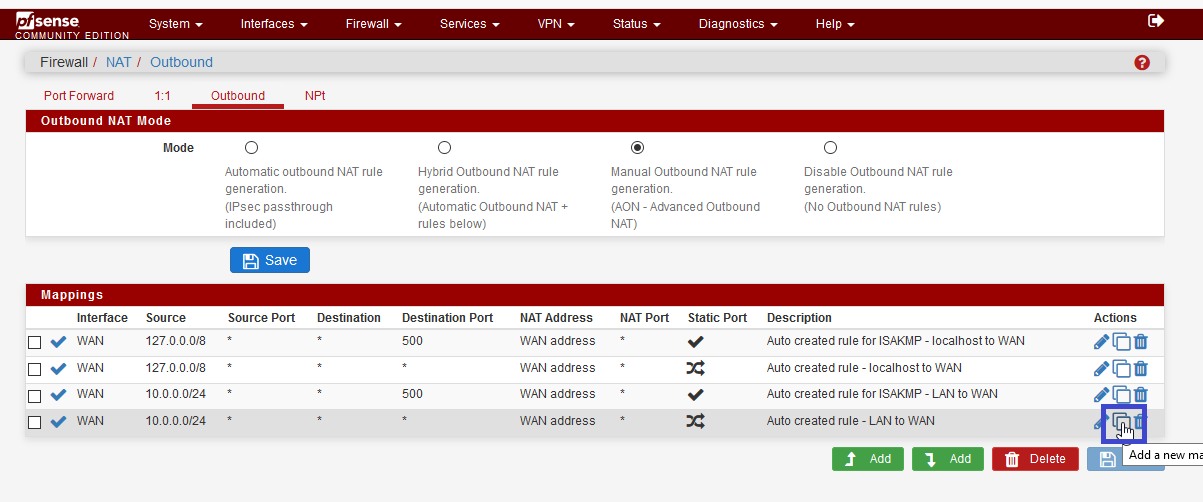
Change WAN interface, by OpenVPN interface, and change the description.
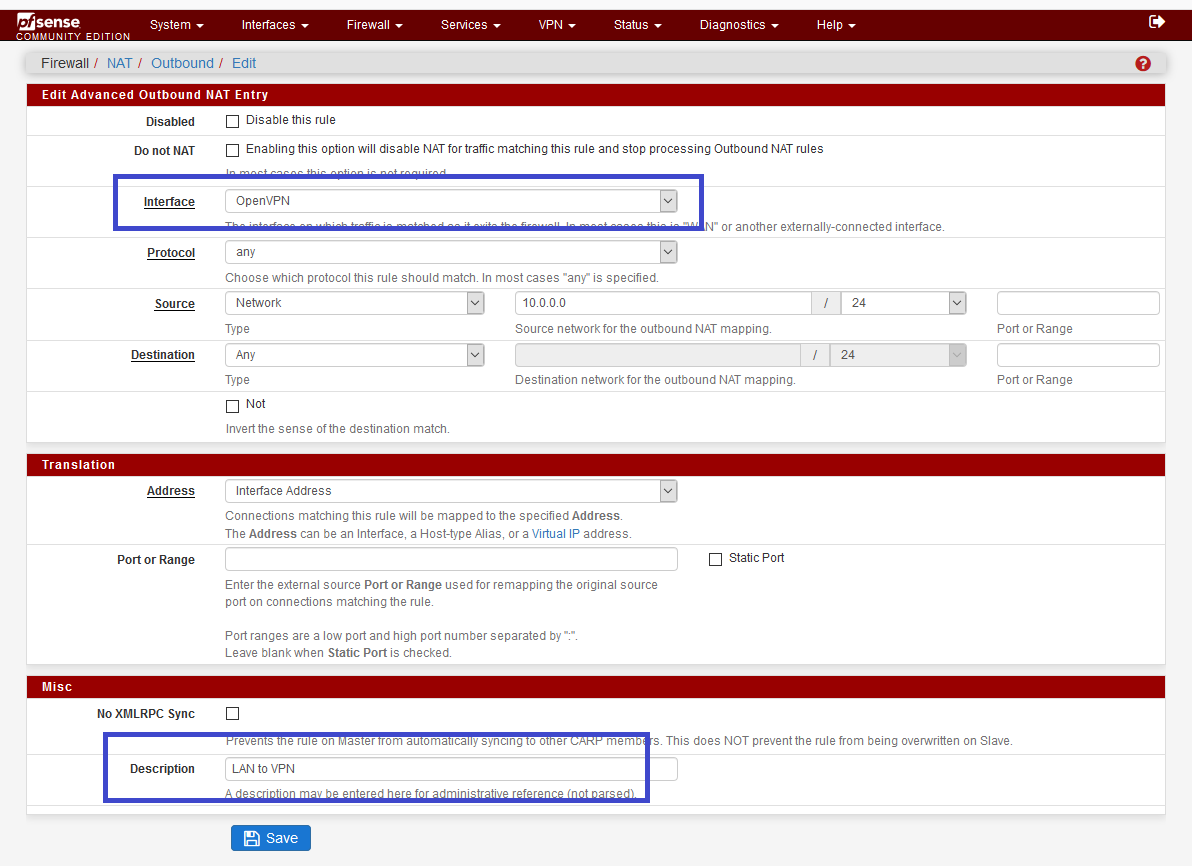
Now, our devices could NAT on OpenVPN "gateway".
Route to VPN from default gateway
Now, we have to work on our default gateway, which is pfsense.pla01.lbdg.lan. We have to declare the new gateway pfsense-vpn-tuto (10.0.0.5) for the LAN.
Livebox_DMZ is my internet connexion (ISP doesn't provide a bridge mode)
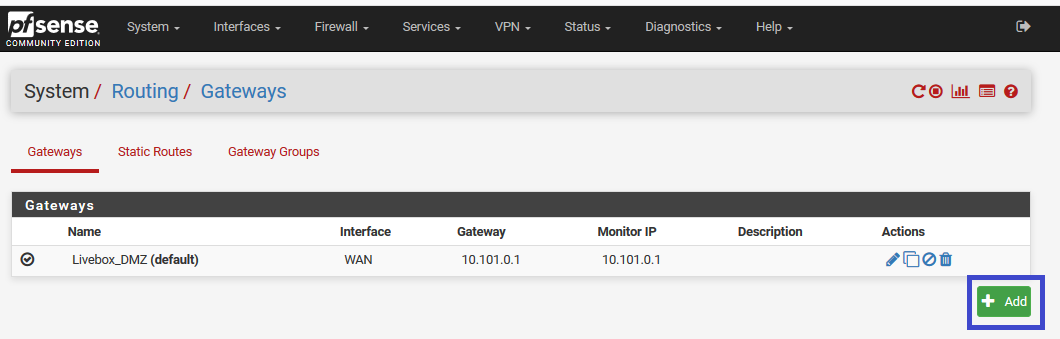
Create the gateway on the LAN
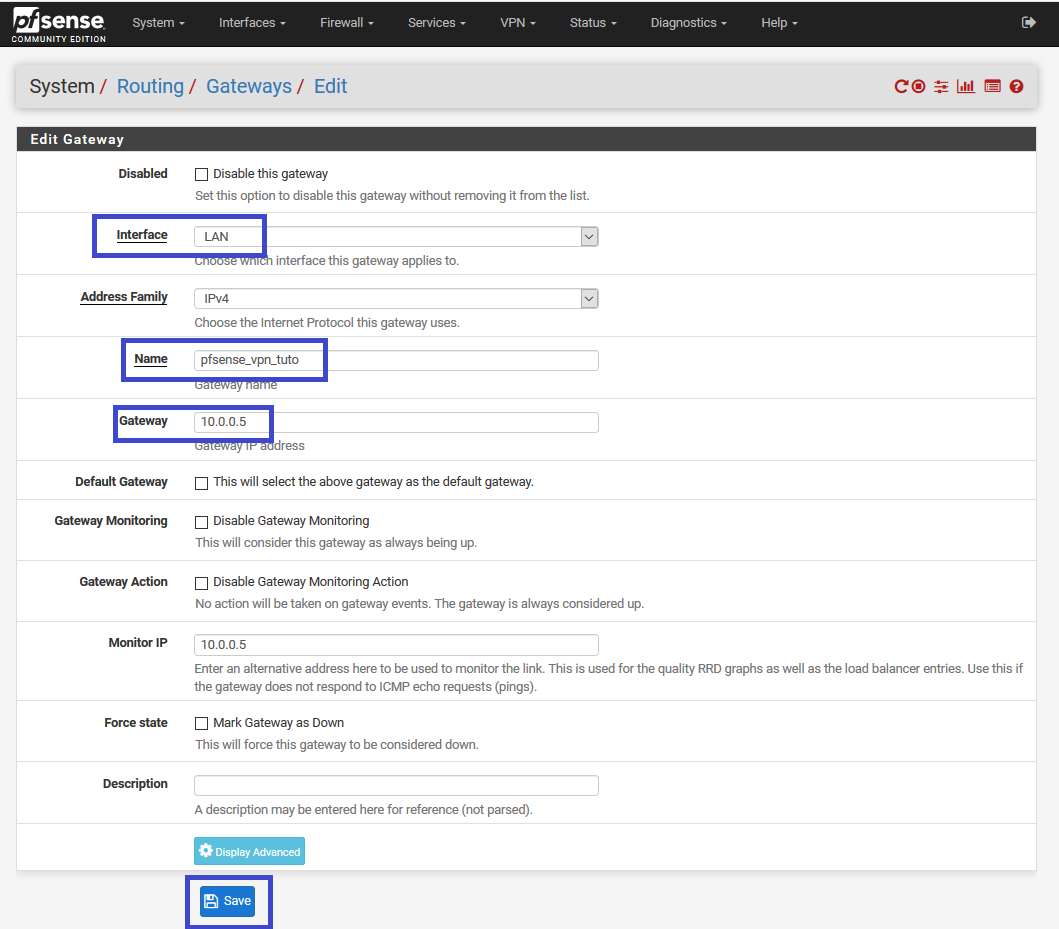
Now, we could use this gateway on rules, what we're gonna do.
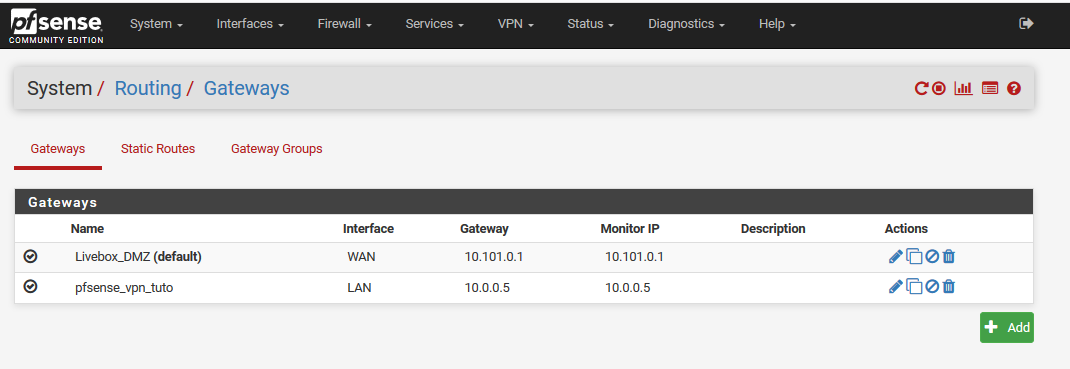
Rules, to route through VPN
Because we want to choose which device will pass through the VPN, we're gonna create specific rules for that :
Create a new simple rule, IPv4, all protocol (will depend on what you want), as source, the device you want to pass through VPN (10.0.0.52 is my laptot), and destination (any)
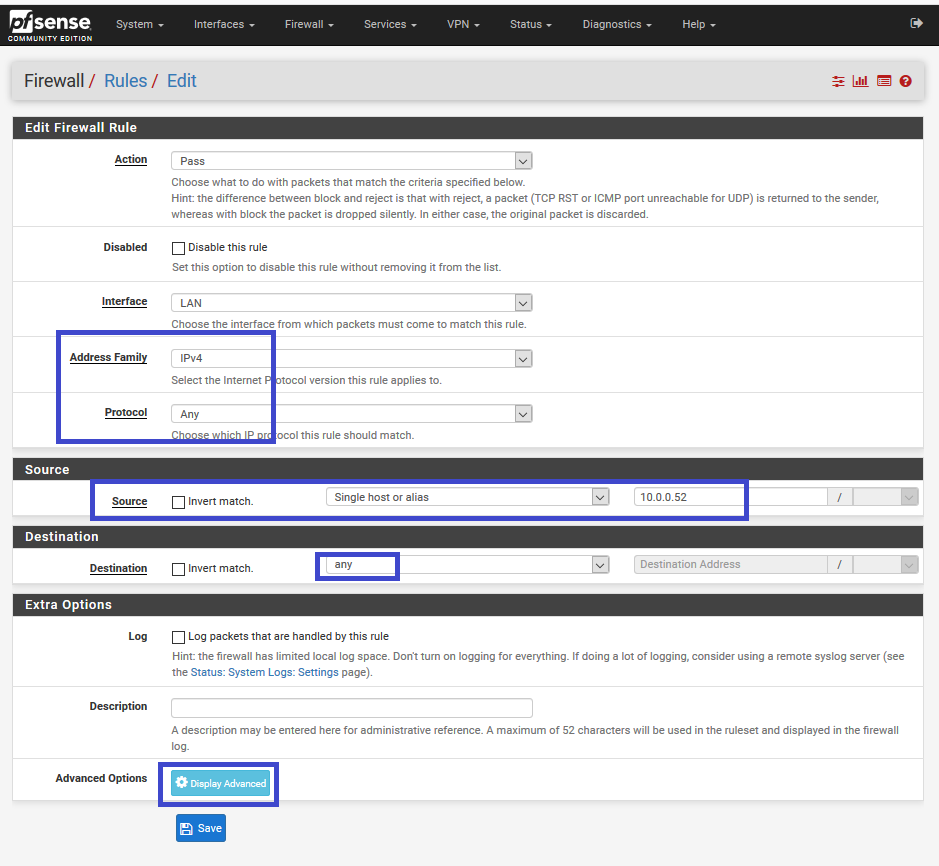
On the advanced option, search for state type and select none
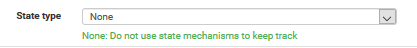
Lower, change the gateway to pfsense_vpn_tuto
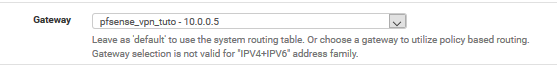
Final rule :
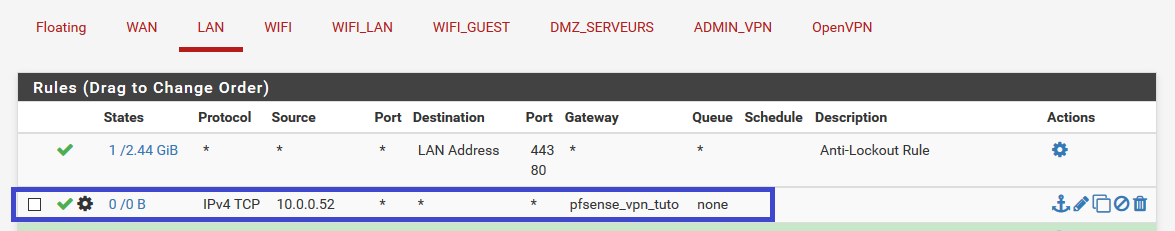
Now, if the rule matchs, connexion will be routed to 10.0.0.5 and NATed to VPN
Results
My previous IP address on internet
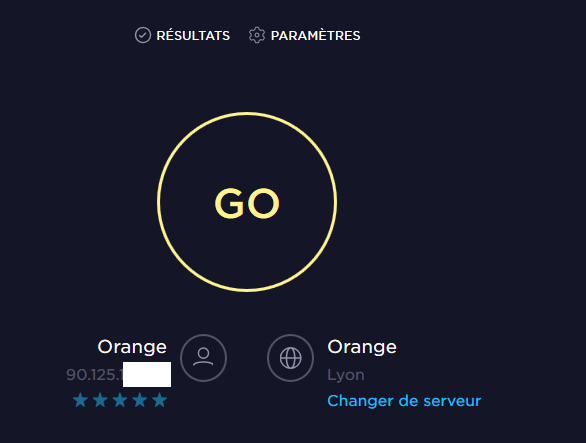
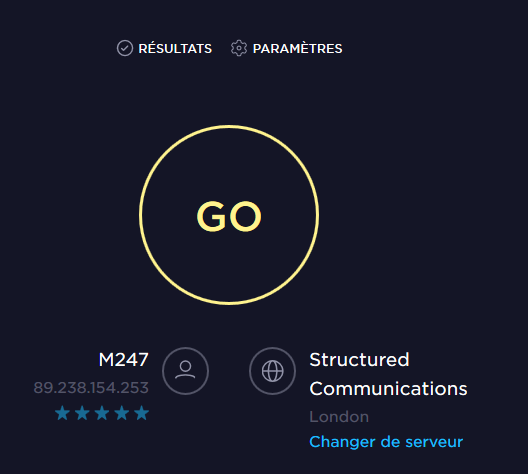
Now, with the VPN and the rules :
Thanks for reading, if you have any question, feel free to react on this reddit thread : Reddit thread
Bonus
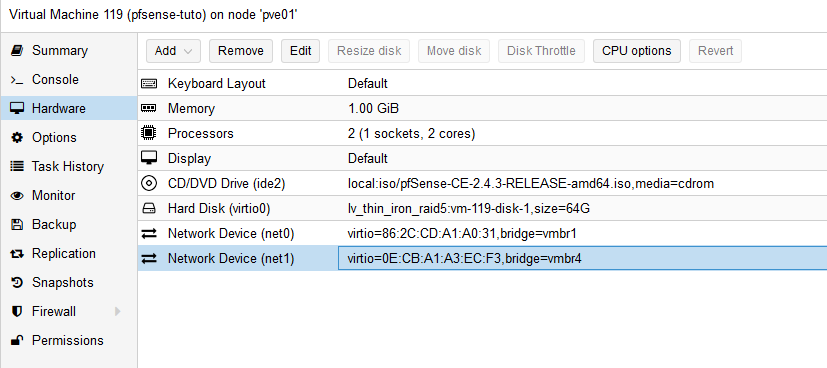
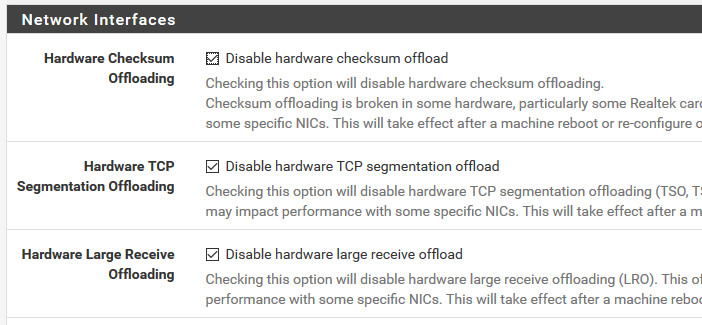
My PfSensen, dedicated to VPN, is virtualized. The only things you need to make sure, are :
- use VirtIO as interface
- disable hardware offload.